Easily visualize vulnerabilities and issues
From the vulnerabilities section, you can access a complete list of all vulnerabilities and issues identified in your application to date. By clicking on each item, you will be able to see detailed information and more information about each issue. This will allow you to stay informed and take the necessary steps to address and resolve potential security risks.
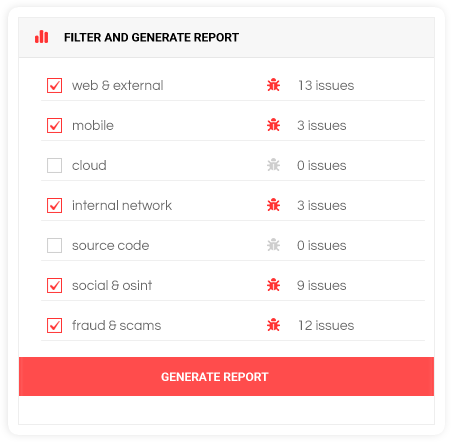
Instant Reporting
Quick and easy reporting: Filter vulnerabilities based on resource type and generate an on-demand report when you need it, ensuring actionable insights quickly.
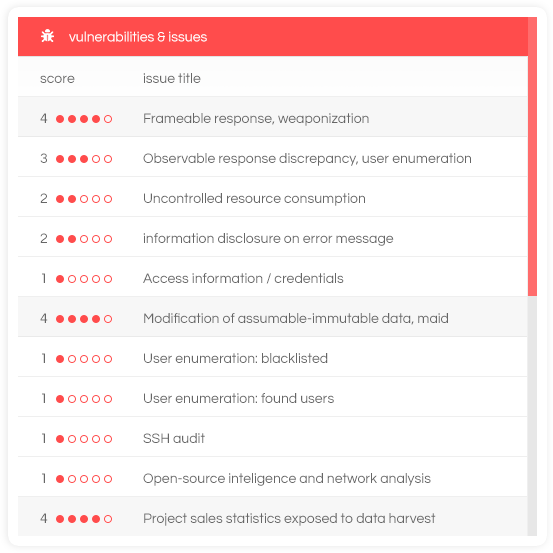
Vulnerability Overview
Quick vulnerability visualization: Easily monitor the criticality associated with each vulnerability, and see which ones are active and which are resolved.

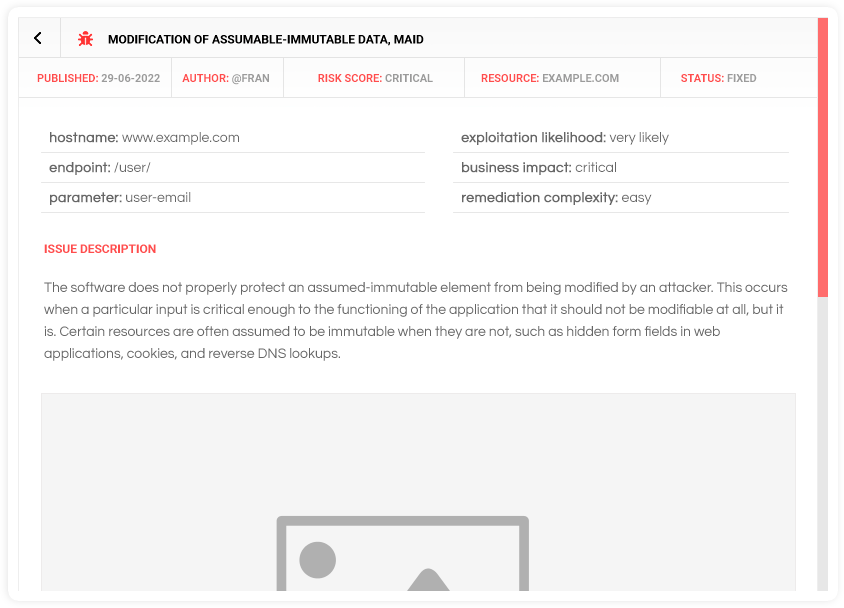
Get full vulnerability details
Get accurate and actionable insights into each identified vulnerability, including its technical description, potential business impact, solution complexity, and recommended steps to effectively resolve it.
Manage your reach
Easily add web and mobile applications, external and internal IP addresses, and more, to gain crucial insights into potential vulnerabilities and risks. Our professional hackers will make sure to uncover any potential issues within your organization’s scope.
System Capabilities
Definition of Scope/Attack Surface:
The app has 6 different modules dedicated exclusively to scope and attack surface. Each of these modules corresponds to a specific type of asset that will undergo penetration/range testing. For example, if you just want to review your web and mobile apps, you can leave the rest of the scope unfilled.
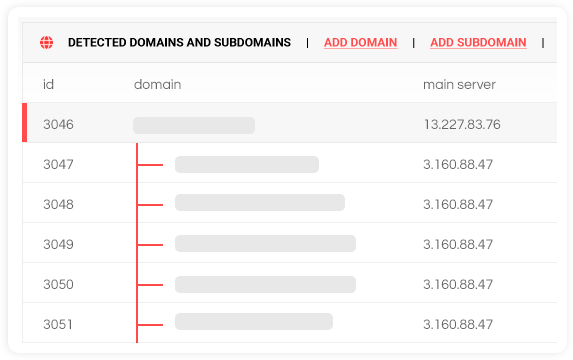
Web Resources:
In this section, you can include domains and subdomains for penetration testing. The app includes a built-in feature to detect subdomains, and our default policy is to detect hidden IT as soon as possible, so that your attack surface or reach can be expanded or reduced when your organization requires it.
Mobile Resources:
In this section, you can analyze mobile apps. You can use it to perform penetration tests and assess the security of your own application, or to analyze the applications that you and your team use on a daily basis and check if your information is adequately protected.
Cloud Resources:
This module contains your organization’s cloud resources. Our capabilities are limited to Amazon Web Services, Microsoft Azure, and GCP.
LAN Resources:
This module allows you to define local area network assets or internal access and provide our team with access to one.
Source code:
Monitor your development cycle and processes with a dedicated specialist with proven expertise in the required stack. If you’re considering adding a dependency to your source code, you might also want to analyze those dependencies to prevent supply chain attacks.
Web Resources:
In this section, you can include domains and subdomains for penetration testing. The app includes a built-in feature to detect subdomains, and our default policy is to detect hidden IT as soon as possible, so that your attack surface or reach can be expanded or reduced when your organization requires it.
Communication and reporting:
The application consists of three specialized modules designed to streamline communication and reporting for your penetration testing needs. Each module has a specific function to improve your experience and efficiency in managing security assessments.
Problems:
Visualize and address vulnerabilities. It allows you to visualize every issue or vulnerability present in your assets. Provides a platform to request assistance within the issue interface if you need additional support. Adapt your approach to manage specific vulnerabilities efficiently.
Create reports:
Create custom reports on demand. It allows you to select a group of issues (e.g., web or mobile resources) and generate detailed, custom reports. Choose specific parameters and criteria for the report that fit your needs. Efficiency: Streamlines the process of generating comprehensive reports for effective communication.
Customer Service:
Address your company’s IT security needs. It offers a dedicated space to request specialized assistance for any specific IT security needs. Personalized Support: Tailor your support requests to your company’s specific security needs. Provide a direct channel for timely and specialized support.
Bitcoin is welcome

For customers and our ethical hackers: We accept all major cryptocurrencies, including bitcoin, ethereum, and litecoin. By accepting these cryptocurrencies, we make it easier for our customers to interact with us.
Linkedin Testimonials









